VIRUS ADVICE http://www1.burtonsys.com/virus_advice.html
http://www2.burtonsys.com/virus_advice.html
virus_advice.txt (plain text, for printing)
By Dave Burton (with a bit of plagiarism from various other sources)
Last updated 22-Jan-2002
(Changes from the 20-Dec-2001 version are in bold.)
CONTENTS:
I. COMPREHENSIVE VIRUS INFORMATION ON THE WEB
II. PRECAUTIONS FOR WINDOWS USERS
III. THE EASIEST DEFENSE
IV. FREE VIRUS REMOVAL AND PROTECTION TOOLS
V. FIREWALLS
VI. HOAXES
I. COMPREHENSIVE VIRUS INFORMATION ON THE WEB:
More information about almost all computer viruses is available
on the following excellent web sites, which are run by five
companies that make anti-virus tools:
http://www.symantec.com/avcenter/vinfodb.html
http://vil.mcafee.com/
http://www.f-secure.com/v-descs/
http://www.antivirus.com/vinfo/
http://www.sophos.com/virusinfo/analyses/
These two sites have a lot of excellent information about viruses,
virus hoaxes, anti-virus tools, etc.:
http://www.virusall.com/
http://www.ciac.org/ciac/
The FBI and Stiller Research sites also have information about
computer security issues:
http://www.nipc.gov/ (FBI)
http://www.stiller.com/
II. PRECAUTIONS FOR WINDOWS USERS:
a) One virus that is going around is the Badtrans worm, and the
newer Badtrans.B variant. Users of Outlook Express (or Outlook)
should make the following setting change to prevent viruses like
Badtrans and Badtrans.B from running automatically when viewed in
the Outlook or Outlook Express preview pane.
First, you need to start Outlook Express (not Internet Explorer).
Then set:
Outlook Express:
Tools -> Options -> Security -> Restricted Sites Zone
(Note: some newer computers with pre-installed software
might come with this set by defaut, which is good.)
This applies to Outlook Express 5.0-6.0. There are probably
some similar settings that need to be adjusted in Outlook, but
I don't know what they are.
Also, with some versions of Outlook Express and Internet Explorer
5.xx, it might be necessary to make an additional setting change,
in Internet Explorer:
Internet Explorer 5.xx:
Tools -> Internet Options -> Security ->
Restricted Sites -> Custom Level ->
Downloads / File Download -> Disable
(Note: if it was already disabled, that is good.)
This won't protect you if you "open" an infected executable email
attachment. So don't! Most people should never need to open any
attachments except .jpg or .jpeg files (photos), and perhaps .rtf
or .txt files (documents).
Also, the same rules apply when someone sends you a file via IRC.
Some viruses spread that way, too.
However, Windows' default file viewing options can hide the true
file extension, so that you can be fooled into opening a .com, .exe,
.doc, .xls, .xlw, .vbs, .bat, .pif, .scr, or other infected file
if it is named "file.jpg.exe" or similar. Until you change the
option, Windows hides the last dot and extension, supposedly as a
"user-friendly" feature. To reduce your likelihood of being fooled,
change the option:
First, start Windows Explorer or Windows NT Explorer, then find
the Options menu item under either View or Tools. Then select the
"View" pane. Then uncheck the checkbox option labeled "Hide file
extensions for known file types" or similar, or click the radio
button for "Show hidden files and folders." (Microsoft seems to
rearrange and reword the menus in every new version of Windows):
Windows Explorer or Windows NT Explorer:
Tools -> Folder Options -> View ->
(or: View -> Options -> View -> )
then select "Show hidden files and folders"
or uncheck "Hide file extensions for known file types"
or uncheck "Hide MS-DOS file extensions for file types that are registered"
Unfortunately, changing the option does NOT work for .pif files.
See for yourself, by performing a little experiment:
1) Copy an innocuous program file, like calc.exe, to c:\README.TXT.pif
2) Run Windows Explorer or Windows NT Explorer and view the files in c:\
3) Note that README.TXT.pif is shown as README.TXT
4) Double-click on it, and see that the program (calc.exe) runs
If that program had been a malicious file attachment, it could
have wiped out your hard disk drive! (Thank you, Microsoft.)
But there IS a subtle visible clue, which can tip you off about
the threat. Look again at "README.TXT" (really README.TXT.pif)
in Windows Explorer. Note the "MS DOS" shortcut icon  beside it
(or, under Win95, a plain "shortcut" icon). That's the clue,
indicating that it is an executable program. If it had really been
a text file, it would have had a Notepad icon
beside it
(or, under Win95, a plain "shortcut" icon). That's the clue,
indicating that it is an executable program. If it had really been
a text file, it would have had a Notepad icon  beside it.
So: BEWARE of files with MS DOS icons
beside it.
So: BEWARE of files with MS DOS icons 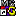 -- they are EXECUTABLE
programs, regardless of the apparent file extension. Do not
double-click them!
b) Also, if you are using Microsoft Internet Explorer 5.xx or 6.0,
you should apply the latest "security rollup" or "cumulative patch"
fixes.
For IE 6.0, all you need is the "cumulative patch" (a 2.3 MB download),
which you can obtain here:
http://www.microsoft.com/technet/security/bulletin/MS01-058.asp
For IE 5.5, it is now a two-step process. An earlier security
rollup was included in IE 5.5's Service Pack 2, but it has been
superceeded by a new "cumulative patch" which requires that SP2 already
be installed. First you must install SP2 (a 17 MB download), which
you can obtain here:
http://www.microsoft.com/Windows/ie/downloads/recommended/ie55sp2/default.asp
Then you can apply the cumulative patch (a 2.2 MB download), which
you can obtain here:
http://www.microsoft.com/technet/security/bulletin/MS01-058.asp
It appears that Microsoft has ceased releasing fixes for IE 5.01,
so the best you can do is to apply the last "security rollup" and
one additional security patch. It is a three-step process. First,
you must apply Service Pack 2 (a 17 MB download), which you can
obtain here:
http://www.microsoft.com/Windows/ie/downloads/recommended/ie501sp2/default.asp
Then apply the security rollup (a 0.35 MB download), which you
can obtain here:
http://support.microsoft.com/default.aspx?scid=kb;en-us;Q295106
Finally, apply the security patch (a 0.5 MB download), which you
can obtain here:
http://www.microsoft.com/technet/security/bulletin/MS01-051.asp
c) Also, if you run Windows XP, you should disable its dangerous
"SSDP Discovery Service" (UPnP) as described here:
http://grc.com/UnPnP/UnPnP.htm
III. THE EASIEST DEFENSE:
The easiest defense against most computer viruses (assuming that
your computer is not already infected!) is simply to use a Yahoo
account for your email, instead of using Microsoft's email clients.
Yahoo (like some other free web-based email sites) has integrated
a commercial virus-scanner into their email system.
If you let suspicious incoming emails "age" for a day or so before
scanning the attachments on Yahoo, you will be 99% safe from
virus-laden emails.
This is a very good solution for Internet novices.
IV. FREE VIRUS REMOVAL AND PROTECTION TOOLS:
The most common viruses going around at the moment are Magistr,
Sircam, Goner, Badtrans, and Hybris. There are free removal tools
for most of these available from the "big two" anti-virus companies
(Norton/Symantec and McAfee/NAI). Norton/Symantec has free removal
tools for Sircam, Goner, Badtrans, Hybris, Nimba, and several
others (but not Magistr or CIH/Chernobyl).
This site has a comprehensive list of virus removal tools:
http://virusall.com/downrem.html
Symantec/Norton has many free virus removal tools, here:
http://www.symantec.com/avcenter/tools.list.html
McAfee/NAI also has a few, here:
http://www.mcafeeb2b.com/naicommon/avert/avert-research-center/tools.asp
Sophos also has some, including free Magistr and CIH/Chernobyl
removal tools:
http://www.sophos.com/support/faqs/
Until recently, a company called Central Command also
offered free Magistr.A and Magistr.B virus removal tools, here:
http://www.centralcommand.com/removal_tools.html
hut they have removed the web page and withdrawn the tools.
I wrote to them and asked about it. They replied to me saying,
"The tool which you are referring to is no longer avaialble, as
we are in the process of preparing for a new product line."
"The Cleaner" is a product which claims to be able to remove many
kinds of worms & viruse, including Magistr. It has a 30 day free
trial period: http://www.moosoft.com/download.php
Caveat: I've not tried it.
Other than the one from Sophos, I don't know of any free tools
specifically to remove Magistr, but perhaps one or more of the free
general-purpose anti-virus packages can do it.
Yes, you read that correctly. Some of the less well-known
general-purpose anti-virus packages can be had for free, for home
use. They appear to be very credible alternatives to the expensive
big two (Norton & McAfee):
http://www.grisoft.com/
http://www.frisk.is/f-prot/download/ (DOS version is free)
http://www.free-av.com/
Plus these two, which require a web connection when you use them:
http://www.pandasoftware.com/activescan/com/
http://housecall.antivirus.com/
Plus, many of the non-free anti-virus utilities have free 30-day
demo versions or shareware versions available, at the usual
shareware web sites, e.g.:
http://www.tucows.com/system/virus95.html
But don't get "Admiral VirusScanner" or "In Vircible Anti virus"
because they are "spyware" -- see the usual spyware list sites:
http://www.spychecker.com/ & http://www.tom-cat.com/spybase/spylist.html
V. FIREWALLS:
Firewall programs are not really anti-virus tools, though they can
help to prevent some kinds of virus infection. But they are useful
for preventing other kinds of security problems, like having your
computer's hard disk drive accidentally appear in the Microsoft
Network Neighborhood of your neighbor down the road, who happens to
have a cablemodem like yours.
Especially if you have an "always on" high speed DSL or cablemodem
internet connection, you should use some sort of firewall.
Two very good, free (for personal use) firewalls for MS Windows are
"ZoneAlarm" and "Tiny Personal FireWall," available here:
http://www.zonelabs.com/products/za/
http://download.cnet.com/downloads/0-10105-108-71881.html?tag=st.dl.10105.upd.10105-108-71881
Both ZoneAlarm and TPFW are much better than some of the non-free
firewalls, such as "BlackICE Defender" and the Symantec/Norton
product. ZoneAlarm is probably easier to install than TPFW, but
TPFW might be a bit more flexible, and is preferred by some
technically savy users.
The best source of information for MS Windows users about Firewalls
and related security issues is Steve Gibson's site:
http://www.grc.com/
Steve's "Shields Up" test can tell you whether your computer and
Internet connection have the most common internet security "leaks."
Testing your system is free and very easy, and well worth your time.
Steve rates Windows firewalls here: http://grc.com/lt/scoreboard.htm
VI. HOAXES:
"Virus warning" emails which ask you to forward them on to lots
of other people are almost always hoaxes. Don't forward them.
(This includes the sulfnbk.exe virus hoax.)
In fact, ALMOST ALL emails which ask you to forward them on to
lots of other people are untrue. Most are pure hoaxes, a few are
partially true, and almost none are entirely true.
If you receive any message that asks you to forward it on to
lots of other people, you can be almost certain that it is a
hoax or a scam. I've seem 'em all: the virus warnings, the
Proctor and Gamble smears, the lost or dying child heartstring-
tuggers, the MLM scams, the Madaline Murray O'Hair / FCC
story, the internet tax hoaxes, etc., etc.. They are all false.
Only if such an email chain-letter references a verifiable,
recognizable, on-line source for more information (such as
www.microsoft.com/something) should you even CONSIDER the
possibility that it might be true. Even then it probably is not.
Usually, the easiest way to verify that email chain-letters are
untrue is to look for them on one of the "hoax buster" web sites.
Also, virus warning chain-letters can be checked on the usual
virus information web sites (Section I, above).
Here are some "hoax buster" web sites for checking suspected email
hoaxes. I suggest bookmarking at least the first two of these
links (if using Internet Explorer, add them to your "favorites"):
http://UrbanLegends.MiningCo.com/
http://www.truthorfiction.com/
http://www.snopes.com/info/search/search.htm
http://www.hoaxinfo.com/
http://www.breakthechain.org/
http://hoaxbusters.ciac.org/
One caution about snopes.com: They have a very comprehensive
and useful hoax database, but they also have a political slant
that makes them an unreliable source of information about emails
with political topics.
-Dave Burton <dburton@burtonsys.com>
Burton Systems Software: http://www.burtonsys.com/
Tel: 1-919-481-0149
-- they are EXECUTABLE
programs, regardless of the apparent file extension. Do not
double-click them!
b) Also, if you are using Microsoft Internet Explorer 5.xx or 6.0,
you should apply the latest "security rollup" or "cumulative patch"
fixes.
For IE 6.0, all you need is the "cumulative patch" (a 2.3 MB download),
which you can obtain here:
http://www.microsoft.com/technet/security/bulletin/MS01-058.asp
For IE 5.5, it is now a two-step process. An earlier security
rollup was included in IE 5.5's Service Pack 2, but it has been
superceeded by a new "cumulative patch" which requires that SP2 already
be installed. First you must install SP2 (a 17 MB download), which
you can obtain here:
http://www.microsoft.com/Windows/ie/downloads/recommended/ie55sp2/default.asp
Then you can apply the cumulative patch (a 2.2 MB download), which
you can obtain here:
http://www.microsoft.com/technet/security/bulletin/MS01-058.asp
It appears that Microsoft has ceased releasing fixes for IE 5.01,
so the best you can do is to apply the last "security rollup" and
one additional security patch. It is a three-step process. First,
you must apply Service Pack 2 (a 17 MB download), which you can
obtain here:
http://www.microsoft.com/Windows/ie/downloads/recommended/ie501sp2/default.asp
Then apply the security rollup (a 0.35 MB download), which you
can obtain here:
http://support.microsoft.com/default.aspx?scid=kb;en-us;Q295106
Finally, apply the security patch (a 0.5 MB download), which you
can obtain here:
http://www.microsoft.com/technet/security/bulletin/MS01-051.asp
c) Also, if you run Windows XP, you should disable its dangerous
"SSDP Discovery Service" (UPnP) as described here:
http://grc.com/UnPnP/UnPnP.htm
III. THE EASIEST DEFENSE:
The easiest defense against most computer viruses (assuming that
your computer is not already infected!) is simply to use a Yahoo
account for your email, instead of using Microsoft's email clients.
Yahoo (like some other free web-based email sites) has integrated
a commercial virus-scanner into their email system.
If you let suspicious incoming emails "age" for a day or so before
scanning the attachments on Yahoo, you will be 99% safe from
virus-laden emails.
This is a very good solution for Internet novices.
IV. FREE VIRUS REMOVAL AND PROTECTION TOOLS:
The most common viruses going around at the moment are Magistr,
Sircam, Goner, Badtrans, and Hybris. There are free removal tools
for most of these available from the "big two" anti-virus companies
(Norton/Symantec and McAfee/NAI). Norton/Symantec has free removal
tools for Sircam, Goner, Badtrans, Hybris, Nimba, and several
others (but not Magistr or CIH/Chernobyl).
This site has a comprehensive list of virus removal tools:
http://virusall.com/downrem.html
Symantec/Norton has many free virus removal tools, here:
http://www.symantec.com/avcenter/tools.list.html
McAfee/NAI also has a few, here:
http://www.mcafeeb2b.com/naicommon/avert/avert-research-center/tools.asp
Sophos also has some, including free Magistr and CIH/Chernobyl
removal tools:
http://www.sophos.com/support/faqs/
Until recently, a company called Central Command also
offered free Magistr.A and Magistr.B virus removal tools, here:
http://www.centralcommand.com/removal_tools.html
hut they have removed the web page and withdrawn the tools.
I wrote to them and asked about it. They replied to me saying,
"The tool which you are referring to is no longer avaialble, as
we are in the process of preparing for a new product line."
"The Cleaner" is a product which claims to be able to remove many
kinds of worms & viruse, including Magistr. It has a 30 day free
trial period: http://www.moosoft.com/download.php
Caveat: I've not tried it.
Other than the one from Sophos, I don't know of any free tools
specifically to remove Magistr, but perhaps one or more of the free
general-purpose anti-virus packages can do it.
Yes, you read that correctly. Some of the less well-known
general-purpose anti-virus packages can be had for free, for home
use. They appear to be very credible alternatives to the expensive
big two (Norton & McAfee):
http://www.grisoft.com/
http://www.frisk.is/f-prot/download/ (DOS version is free)
http://www.free-av.com/
Plus these two, which require a web connection when you use them:
http://www.pandasoftware.com/activescan/com/
http://housecall.antivirus.com/
Plus, many of the non-free anti-virus utilities have free 30-day
demo versions or shareware versions available, at the usual
shareware web sites, e.g.:
http://www.tucows.com/system/virus95.html
But don't get "Admiral VirusScanner" or "In Vircible Anti virus"
because they are "spyware" -- see the usual spyware list sites:
http://www.spychecker.com/ & http://www.tom-cat.com/spybase/spylist.html
V. FIREWALLS:
Firewall programs are not really anti-virus tools, though they can
help to prevent some kinds of virus infection. But they are useful
for preventing other kinds of security problems, like having your
computer's hard disk drive accidentally appear in the Microsoft
Network Neighborhood of your neighbor down the road, who happens to
have a cablemodem like yours.
Especially if you have an "always on" high speed DSL or cablemodem
internet connection, you should use some sort of firewall.
Two very good, free (for personal use) firewalls for MS Windows are
"ZoneAlarm" and "Tiny Personal FireWall," available here:
http://www.zonelabs.com/products/za/
http://download.cnet.com/downloads/0-10105-108-71881.html?tag=st.dl.10105.upd.10105-108-71881
Both ZoneAlarm and TPFW are much better than some of the non-free
firewalls, such as "BlackICE Defender" and the Symantec/Norton
product. ZoneAlarm is probably easier to install than TPFW, but
TPFW might be a bit more flexible, and is preferred by some
technically savy users.
The best source of information for MS Windows users about Firewalls
and related security issues is Steve Gibson's site:
http://www.grc.com/
Steve's "Shields Up" test can tell you whether your computer and
Internet connection have the most common internet security "leaks."
Testing your system is free and very easy, and well worth your time.
Steve rates Windows firewalls here: http://grc.com/lt/scoreboard.htm
VI. HOAXES:
"Virus warning" emails which ask you to forward them on to lots
of other people are almost always hoaxes. Don't forward them.
(This includes the sulfnbk.exe virus hoax.)
In fact, ALMOST ALL emails which ask you to forward them on to
lots of other people are untrue. Most are pure hoaxes, a few are
partially true, and almost none are entirely true.
If you receive any message that asks you to forward it on to
lots of other people, you can be almost certain that it is a
hoax or a scam. I've seem 'em all: the virus warnings, the
Proctor and Gamble smears, the lost or dying child heartstring-
tuggers, the MLM scams, the Madaline Murray O'Hair / FCC
story, the internet tax hoaxes, etc., etc.. They are all false.
Only if such an email chain-letter references a verifiable,
recognizable, on-line source for more information (such as
www.microsoft.com/something) should you even CONSIDER the
possibility that it might be true. Even then it probably is not.
Usually, the easiest way to verify that email chain-letters are
untrue is to look for them on one of the "hoax buster" web sites.
Also, virus warning chain-letters can be checked on the usual
virus information web sites (Section I, above).
Here are some "hoax buster" web sites for checking suspected email
hoaxes. I suggest bookmarking at least the first two of these
links (if using Internet Explorer, add them to your "favorites"):
http://UrbanLegends.MiningCo.com/
http://www.truthorfiction.com/
http://www.snopes.com/info/search/search.htm
http://www.hoaxinfo.com/
http://www.breakthechain.org/
http://hoaxbusters.ciac.org/
One caution about snopes.com: They have a very comprehensive
and useful hoax database, but they also have a political slant
that makes them an unreliable source of information about emails
with political topics.
-Dave Burton <dburton@burtonsys.com>
Burton Systems Software: http://www.burtonsys.com/
Tel: 1-919-481-0149
 beside it
(or, under Win95, a plain "shortcut" icon). That's the clue,
indicating that it is an executable program. If it had really been
a text file, it would have had a Notepad icon
beside it
(or, under Win95, a plain "shortcut" icon). That's the clue,
indicating that it is an executable program. If it had really been
a text file, it would have had a Notepad icon  beside it.
So: BEWARE of files with MS DOS icons
beside it.
So: BEWARE of files with MS DOS icons 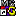 -- they are EXECUTABLE
programs, regardless of the apparent file extension. Do not
double-click them!
b) Also, if you are using Microsoft Internet Explorer 5.xx or 6.0,
you should apply the latest "security rollup" or "cumulative patch"
fixes.
For IE 6.0, all you need is the "cumulative patch" (a 2.3 MB download),
which you can obtain here:
http://www.microsoft.com/technet/security/bulletin/MS01-058.asp
For IE 5.5, it is now a two-step process. An earlier security
rollup was included in IE 5.5's Service Pack 2, but it has been
superceeded by a new "cumulative patch" which requires that SP2 already
be installed. First you must install SP2 (a 17 MB download), which
you can obtain here:
http://www.microsoft.com/Windows/ie/downloads/recommended/ie55sp2/default.asp
Then you can apply the cumulative patch (a 2.2 MB download), which
you can obtain here:
http://www.microsoft.com/technet/security/bulletin/MS01-058.asp
It appears that Microsoft has ceased releasing fixes for IE 5.01,
so the best you can do is to apply the last "security rollup" and
one additional security patch. It is a three-step process. First,
you must apply Service Pack 2 (a 17 MB download), which you can
obtain here:
http://www.microsoft.com/Windows/ie/downloads/recommended/ie501sp2/default.asp
Then apply the security rollup (a 0.35 MB download), which you
can obtain here:
http://support.microsoft.com/default.aspx?scid=kb;en-us;Q295106
Finally, apply the security patch (a 0.5 MB download), which you
can obtain here:
http://www.microsoft.com/technet/security/bulletin/MS01-051.asp
c) Also, if you run Windows XP, you should disable its dangerous
"SSDP Discovery Service" (UPnP) as described here:
http://grc.com/UnPnP/UnPnP.htm
III. THE EASIEST DEFENSE:
The easiest defense against most computer viruses (assuming that
your computer is not already infected!) is simply to use a Yahoo
account for your email, instead of using Microsoft's email clients.
Yahoo (like some other free web-based email sites) has integrated
a commercial virus-scanner into their email system.
If you let suspicious incoming emails "age" for a day or so before
scanning the attachments on Yahoo, you will be 99% safe from
virus-laden emails.
This is a very good solution for Internet novices.
IV. FREE VIRUS REMOVAL AND PROTECTION TOOLS:
The most common viruses going around at the moment are Magistr,
Sircam, Goner, Badtrans, and Hybris. There are free removal tools
for most of these available from the "big two" anti-virus companies
(Norton/Symantec and McAfee/NAI). Norton/Symantec has free removal
tools for Sircam, Goner, Badtrans, Hybris, Nimba, and several
others (but not Magistr or CIH/Chernobyl).
This site has a comprehensive list of virus removal tools:
http://virusall.com/downrem.html
Symantec/Norton has many free virus removal tools, here:
http://www.symantec.com/avcenter/tools.list.html
McAfee/NAI also has a few, here:
http://www.mcafeeb2b.com/naicommon/avert/avert-research-center/tools.asp
Sophos also has some, including free Magistr and CIH/Chernobyl
removal tools:
http://www.sophos.com/support/faqs/
Until recently, a company called Central Command also
offered free Magistr.A and Magistr.B virus removal tools, here:
http://www.centralcommand.com/removal_tools.html
hut they have removed the web page and withdrawn the tools.
I wrote to them and asked about it. They replied to me saying,
"The tool which you are referring to is no longer avaialble, as
we are in the process of preparing for a new product line."
"The Cleaner" is a product which claims to be able to remove many
kinds of worms & viruse, including Magistr. It has a 30 day free
trial period: http://www.moosoft.com/download.php
Caveat: I've not tried it.
Other than the one from Sophos, I don't know of any free tools
specifically to remove Magistr, but perhaps one or more of the free
general-purpose anti-virus packages can do it.
Yes, you read that correctly. Some of the less well-known
general-purpose anti-virus packages can be had for free, for home
use. They appear to be very credible alternatives to the expensive
big two (Norton & McAfee):
http://www.grisoft.com/
http://www.frisk.is/f-prot/download/ (DOS version is free)
http://www.free-av.com/
Plus these two, which require a web connection when you use them:
http://www.pandasoftware.com/activescan/com/
http://housecall.antivirus.com/
Plus, many of the non-free anti-virus utilities have free 30-day
demo versions or shareware versions available, at the usual
shareware web sites, e.g.:
http://www.tucows.com/system/virus95.html
But don't get "Admiral VirusScanner" or "In Vircible Anti virus"
because they are "spyware" -- see the usual spyware list sites:
http://www.spychecker.com/ & http://www.tom-cat.com/spybase/spylist.html
V. FIREWALLS:
Firewall programs are not really anti-virus tools, though they can
help to prevent some kinds of virus infection. But they are useful
for preventing other kinds of security problems, like having your
computer's hard disk drive accidentally appear in the Microsoft
Network Neighborhood of your neighbor down the road, who happens to
have a cablemodem like yours.
Especially if you have an "always on" high speed DSL or cablemodem
internet connection, you should use some sort of firewall.
Two very good, free (for personal use) firewalls for MS Windows are
"ZoneAlarm" and "Tiny Personal FireWall," available here:
http://www.zonelabs.com/products/za/
http://download.cnet.com/downloads/0-10105-108-71881.html?tag=st.dl.10105.upd.10105-108-71881
Both ZoneAlarm and TPFW are much better than some of the non-free
firewalls, such as "BlackICE Defender" and the Symantec/Norton
product. ZoneAlarm is probably easier to install than TPFW, but
TPFW might be a bit more flexible, and is preferred by some
technically savy users.
The best source of information for MS Windows users about Firewalls
and related security issues is Steve Gibson's site:
http://www.grc.com/
Steve's "Shields Up" test can tell you whether your computer and
Internet connection have the most common internet security "leaks."
Testing your system is free and very easy, and well worth your time.
Steve rates Windows firewalls here: http://grc.com/lt/scoreboard.htm
VI. HOAXES:
"Virus warning" emails which ask you to forward them on to lots
of other people are almost always hoaxes. Don't forward them.
(This includes the sulfnbk.exe virus hoax.)
In fact, ALMOST ALL emails which ask you to forward them on to
lots of other people are untrue. Most are pure hoaxes, a few are
partially true, and almost none are entirely true.
If you receive any message that asks you to forward it on to
lots of other people, you can be almost certain that it is a
hoax or a scam. I've seem 'em all: the virus warnings, the
Proctor and Gamble smears, the lost or dying child heartstring-
tuggers, the MLM scams, the Madaline Murray O'Hair / FCC
story, the internet tax hoaxes, etc., etc.. They are all false.
Only if such an email chain-letter references a verifiable,
recognizable, on-line source for more information (such as
www.microsoft.com/something) should you even CONSIDER the
possibility that it might be true. Even then it probably is not.
Usually, the easiest way to verify that email chain-letters are
untrue is to look for them on one of the "hoax buster" web sites.
Also, virus warning chain-letters can be checked on the usual
virus information web sites (Section I, above).
Here are some "hoax buster" web sites for checking suspected email
hoaxes. I suggest bookmarking at least the first two of these
links (if using Internet Explorer, add them to your "favorites"):
http://UrbanLegends.MiningCo.com/
http://www.truthorfiction.com/
http://www.snopes.com/info/search/search.htm
http://www.hoaxinfo.com/
http://www.breakthechain.org/
http://hoaxbusters.ciac.org/
One caution about snopes.com: They have a very comprehensive
and useful hoax database, but they also have a political slant
that makes them an unreliable source of information about emails
with political topics.
-Dave Burton <dburton@burtonsys.com>
Burton Systems Software: http://www.burtonsys.com/
Tel: 1-919-481-0149
-- they are EXECUTABLE
programs, regardless of the apparent file extension. Do not
double-click them!
b) Also, if you are using Microsoft Internet Explorer 5.xx or 6.0,
you should apply the latest "security rollup" or "cumulative patch"
fixes.
For IE 6.0, all you need is the "cumulative patch" (a 2.3 MB download),
which you can obtain here:
http://www.microsoft.com/technet/security/bulletin/MS01-058.asp
For IE 5.5, it is now a two-step process. An earlier security
rollup was included in IE 5.5's Service Pack 2, but it has been
superceeded by a new "cumulative patch" which requires that SP2 already
be installed. First you must install SP2 (a 17 MB download), which
you can obtain here:
http://www.microsoft.com/Windows/ie/downloads/recommended/ie55sp2/default.asp
Then you can apply the cumulative patch (a 2.2 MB download), which
you can obtain here:
http://www.microsoft.com/technet/security/bulletin/MS01-058.asp
It appears that Microsoft has ceased releasing fixes for IE 5.01,
so the best you can do is to apply the last "security rollup" and
one additional security patch. It is a three-step process. First,
you must apply Service Pack 2 (a 17 MB download), which you can
obtain here:
http://www.microsoft.com/Windows/ie/downloads/recommended/ie501sp2/default.asp
Then apply the security rollup (a 0.35 MB download), which you
can obtain here:
http://support.microsoft.com/default.aspx?scid=kb;en-us;Q295106
Finally, apply the security patch (a 0.5 MB download), which you
can obtain here:
http://www.microsoft.com/technet/security/bulletin/MS01-051.asp
c) Also, if you run Windows XP, you should disable its dangerous
"SSDP Discovery Service" (UPnP) as described here:
http://grc.com/UnPnP/UnPnP.htm
III. THE EASIEST DEFENSE:
The easiest defense against most computer viruses (assuming that
your computer is not already infected!) is simply to use a Yahoo
account for your email, instead of using Microsoft's email clients.
Yahoo (like some other free web-based email sites) has integrated
a commercial virus-scanner into their email system.
If you let suspicious incoming emails "age" for a day or so before
scanning the attachments on Yahoo, you will be 99% safe from
virus-laden emails.
This is a very good solution for Internet novices.
IV. FREE VIRUS REMOVAL AND PROTECTION TOOLS:
The most common viruses going around at the moment are Magistr,
Sircam, Goner, Badtrans, and Hybris. There are free removal tools
for most of these available from the "big two" anti-virus companies
(Norton/Symantec and McAfee/NAI). Norton/Symantec has free removal
tools for Sircam, Goner, Badtrans, Hybris, Nimba, and several
others (but not Magistr or CIH/Chernobyl).
This site has a comprehensive list of virus removal tools:
http://virusall.com/downrem.html
Symantec/Norton has many free virus removal tools, here:
http://www.symantec.com/avcenter/tools.list.html
McAfee/NAI also has a few, here:
http://www.mcafeeb2b.com/naicommon/avert/avert-research-center/tools.asp
Sophos also has some, including free Magistr and CIH/Chernobyl
removal tools:
http://www.sophos.com/support/faqs/
Until recently, a company called Central Command also
offered free Magistr.A and Magistr.B virus removal tools, here:
http://www.centralcommand.com/removal_tools.html
hut they have removed the web page and withdrawn the tools.
I wrote to them and asked about it. They replied to me saying,
"The tool which you are referring to is no longer avaialble, as
we are in the process of preparing for a new product line."
"The Cleaner" is a product which claims to be able to remove many
kinds of worms & viruse, including Magistr. It has a 30 day free
trial period: http://www.moosoft.com/download.php
Caveat: I've not tried it.
Other than the one from Sophos, I don't know of any free tools
specifically to remove Magistr, but perhaps one or more of the free
general-purpose anti-virus packages can do it.
Yes, you read that correctly. Some of the less well-known
general-purpose anti-virus packages can be had for free, for home
use. They appear to be very credible alternatives to the expensive
big two (Norton & McAfee):
http://www.grisoft.com/
http://www.frisk.is/f-prot/download/ (DOS version is free)
http://www.free-av.com/
Plus these two, which require a web connection when you use them:
http://www.pandasoftware.com/activescan/com/
http://housecall.antivirus.com/
Plus, many of the non-free anti-virus utilities have free 30-day
demo versions or shareware versions available, at the usual
shareware web sites, e.g.:
http://www.tucows.com/system/virus95.html
But don't get "Admiral VirusScanner" or "In Vircible Anti virus"
because they are "spyware" -- see the usual spyware list sites:
http://www.spychecker.com/ & http://www.tom-cat.com/spybase/spylist.html
V. FIREWALLS:
Firewall programs are not really anti-virus tools, though they can
help to prevent some kinds of virus infection. But they are useful
for preventing other kinds of security problems, like having your
computer's hard disk drive accidentally appear in the Microsoft
Network Neighborhood of your neighbor down the road, who happens to
have a cablemodem like yours.
Especially if you have an "always on" high speed DSL or cablemodem
internet connection, you should use some sort of firewall.
Two very good, free (for personal use) firewalls for MS Windows are
"ZoneAlarm" and "Tiny Personal FireWall," available here:
http://www.zonelabs.com/products/za/
http://download.cnet.com/downloads/0-10105-108-71881.html?tag=st.dl.10105.upd.10105-108-71881
Both ZoneAlarm and TPFW are much better than some of the non-free
firewalls, such as "BlackICE Defender" and the Symantec/Norton
product. ZoneAlarm is probably easier to install than TPFW, but
TPFW might be a bit more flexible, and is preferred by some
technically savy users.
The best source of information for MS Windows users about Firewalls
and related security issues is Steve Gibson's site:
http://www.grc.com/
Steve's "Shields Up" test can tell you whether your computer and
Internet connection have the most common internet security "leaks."
Testing your system is free and very easy, and well worth your time.
Steve rates Windows firewalls here: http://grc.com/lt/scoreboard.htm
VI. HOAXES:
"Virus warning" emails which ask you to forward them on to lots
of other people are almost always hoaxes. Don't forward them.
(This includes the sulfnbk.exe virus hoax.)
In fact, ALMOST ALL emails which ask you to forward them on to
lots of other people are untrue. Most are pure hoaxes, a few are
partially true, and almost none are entirely true.
If you receive any message that asks you to forward it on to
lots of other people, you can be almost certain that it is a
hoax or a scam. I've seem 'em all: the virus warnings, the
Proctor and Gamble smears, the lost or dying child heartstring-
tuggers, the MLM scams, the Madaline Murray O'Hair / FCC
story, the internet tax hoaxes, etc., etc.. They are all false.
Only if such an email chain-letter references a verifiable,
recognizable, on-line source for more information (such as
www.microsoft.com/something) should you even CONSIDER the
possibility that it might be true. Even then it probably is not.
Usually, the easiest way to verify that email chain-letters are
untrue is to look for them on one of the "hoax buster" web sites.
Also, virus warning chain-letters can be checked on the usual
virus information web sites (Section I, above).
Here are some "hoax buster" web sites for checking suspected email
hoaxes. I suggest bookmarking at least the first two of these
links (if using Internet Explorer, add them to your "favorites"):
http://UrbanLegends.MiningCo.com/
http://www.truthorfiction.com/
http://www.snopes.com/info/search/search.htm
http://www.hoaxinfo.com/
http://www.breakthechain.org/
http://hoaxbusters.ciac.org/
One caution about snopes.com: They have a very comprehensive
and useful hoax database, but they also have a political slant
that makes them an unreliable source of information about emails
with political topics.
-Dave Burton <dburton@burtonsys.com>
Burton Systems Software: http://www.burtonsys.com/
Tel: 1-919-481-0149